OpenID Connect
Trento integrates with an identity provider (IDP) that use the OpenID Connect (OIDC) protocol to authenticate users accessing the console. Authorization for specific abilities/permissions is managed by Trento, which means that only basic user information is retrieved from the external IDP.
Enabling OIDC
The OIDC authentication is disabled by default.
Provide the following environment variables to enable OIDC feature when starting Trento.
# Required: ENABLE_OIDC=true OIDC_CLIENT_ID=<<OIDC_CLIENT_ID>> OIDC_CLIENT_SECRET=<<OIDC_CLIENT_SECRET>> OIDC_BASE_URL=<<OIDC_BASE_URL>> # Optional: OIDC_CALLBACK_URL=<<OIDC_CALLBACK_URL>>
Enabling OIDC in Development
Enable OIDC in the development environment using Docker and Keycloak as IDP.
Starting Keycloak Identity Provider
Use a custom Docker profile to start Keycloak as IDP for local development.
Start the Docker containers with the idp profile:
docker compose --profile idp up
Keycloak server can be accessed at http://localhost:8081
Create OIDC configuration
-
Create a new local development configuration
dev.local.exsinconfigdirectory. -
Enable OIDC in
dev.local.exsconfig:import Config config :trento, :oidc, enabled: true -
Start Trento web as usual
iex -S mix phx.server
Login into Trento web console using Single Sign-on with Keycloak
-
Navigate to the Trento web console.
-
Click on
Login with Single Sign-on:
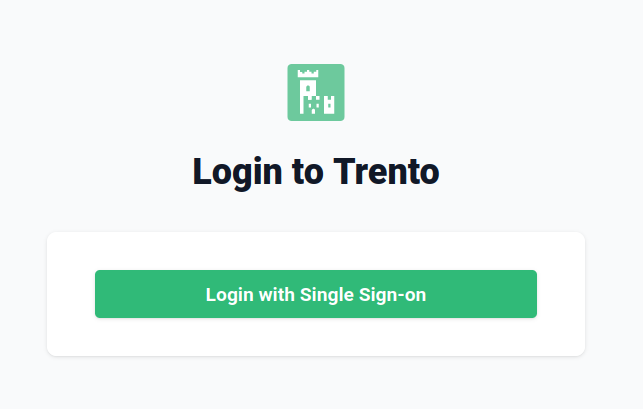
You will be redirected to the Keycloak login page:
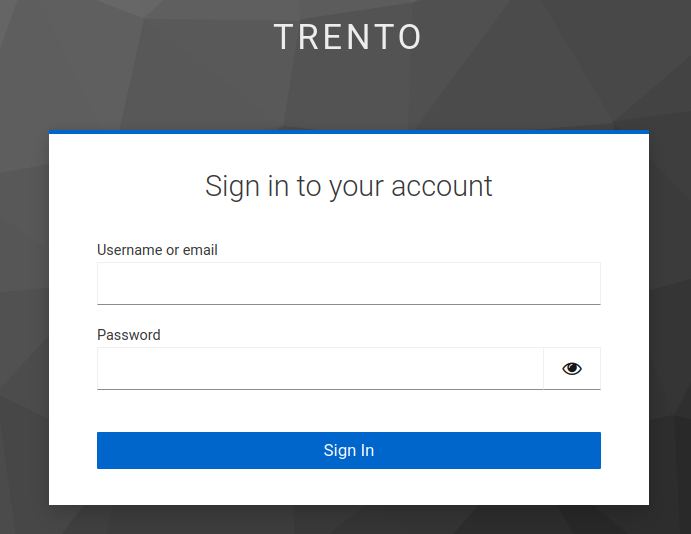
Login as Trento user through keycloak IDP
The default Trento login credentials are:
Username:
trentoidp
Password:
password
After successfully entering user login data, the user is redirected to Trento web console.
Assigning Admin Rights to the Trento User
Grant admin rights to the trentoidp user, update the
config/dev.local.exs file as follows , then restart the application
import Config config :trento, :oidc, enabled: true config :trento, admin_user: "trentoidp"
Run OIDC integration E2E tests
Running OIDC e2e tests, requires a running IDP provider.
Run docker compose with the --profile idp flag, to use our
Keycloak deployment for testing.